Reluctantly, today’s workforce is getting more accustomed to working from home, and data center operators are not immune to this shift in operational flexibility. This along with the impacts of Critical Infrastructure becoming more tangible, has made the need for a Data Center Infrastructure Management (DCIM) systems more apparent. This is not groundbreaking news for those of us in Infrastructure and Operations (I&O) who have always tended to on-prem conditions in a 24x7 environment. While this has historically had flavors of “managing from afar”, the extent of insight and control have been steadily increasing with the abilities enabled by today’s DCIM solutions.

Critical Infrastructure has typically been a world of hardware; physical equipment that is your last line of defense in keeping your facility operational. When problems arose, a tech would address the alarm through a physical inspection - or you’d call a Hardware Hotshot (like DVL) offering expertise in that particular problem. But organizations today expect much more than simply staying operational from their I&O Teams. Leadership Teams expect:
- Risk reduction
- Improving capacity management/forecasting
- Increasing agile decision making
- Compliance to federal regulations and corporate responsibility requirements
These expectations are made a reality thanks to the continual advancements in the DCIM landscape. From native solutions developed by manufacturers like Vertiv, to the after-market solutions supplementing information to management teams across everything from generator, to ATS, to UPS, to CRAC, DCIM enables users a greater sense of control created by granular specifics across the entire critical infrastructure equation. Availability of data is not only providing better insight into the overall performance of the data center, but in some instances it’s actually able to predict the problem before it arises. This data is improving threat management, response times, and paving the way for positive financial impacts to the business.
Most professionals (especially those in the world of operations) have asked themselves, “How can I do more with less?” Well, the old adage of “you can’t manage what you can’t measure” puts into perspective what is needed in order to get more positive results with less… dollars, efforts, and assets. Efficiency of a data center revolves around reducing waste and unnecessary overprovisioning of power, cooling, space, and IT resources. DCIM solutions allow you to tap into the data behind how your infrastructure is performing today, and helps you understand how you can better manage impacts of those variables tomorrow, resulting in improved financials.
While DCIM offers many paths to greener pastures, unfortunately, there have been plenty of DCIM projects that had to be cancelled due to damaging mistakes in solution selection and deployment. This challenge is indicative of why only 42% of data center operators are using a solution today, and emphasizes why DCIM should be a collaborative process across the entire organization. When an organization takes a collective look at the available data, connecting one dot to the next, decision making teams are able to recognize more opportunities for improvement and create a shared perspective on where the organization stands on:
- Required Analytics
- Must-Have Features
- Agreed upon objectives
- Security Policies (i.e. platform resiliency, data integrity)
- Reporting and Mobility
These are only a few points to consider when looking at DCIM as more than just a technology. Technologies are tools to enhance the management philosophy of how you run the business, and how to maximize not just the equipment – but the people providing tangible results in the forms of efficiency and financial improvements. We discussed a few more of these considerations on a recent webinar, Keeping a Critical Eye on Critical Infrastructure; and covered how DCIM has exponentially improved throughout the years with our friends at Critical Labs and Packet Power. The panel discussion ended up being a great overview of the DCIM landscape, and the value-added impacts that are behind today’s data centers.
 |
 |
We invite you to listen to last week’s webinar to learn much more about DCIM and monitoring systems and how they can, in most cases, be easily integrated into your existing infrastructure.



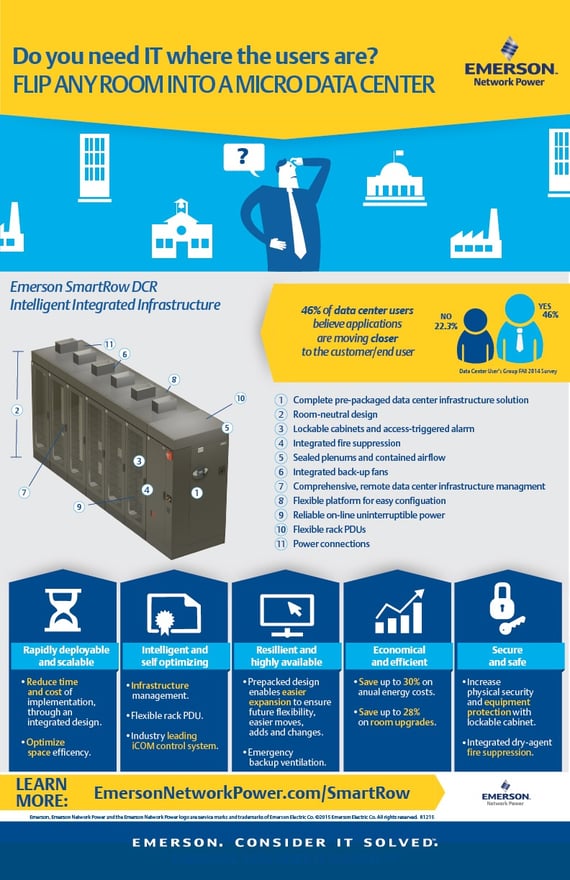
 In this Vertiv case study, we gain insight into a job done for Pasco County, FL. Pasco County was looking to update their data center, while maintaining safety and availability. With the implementation of the Vertiv SmartRow™, Pasco County was able to do all this while increasing efficiency and staying within budget. Now Pasco County’s data center environment aligns with their increasing IT needs.
In this Vertiv case study, we gain insight into a job done for Pasco County, FL. Pasco County was looking to update their data center, while maintaining safety and availability. With the implementation of the Vertiv SmartRow™, Pasco County was able to do all this while increasing efficiency and staying within budget. Now Pasco County’s data center environment aligns with their increasing IT needs.