Learn More Here
For HVAC Emergencies: 1-866-DVL-HVAC | For UPS Emergencies: 1-800-LIEBERT
For Generator Emergencies in CO, NM, or WY:303-953-3128
For HVAC Emergencies, please call 1-866-DVL-HVAC
by Marissa Donatone on 12/29/15 8:31 AM

Learn More Here
Topics: Emerson Network Power, Data Center, data center design, DVL, monitoring, smart solutions, IT, smartrow
by Emerson Network Power on 10/8/15 9:09 AM
Ronny Mees | Emerson Network Power

Today’s most innovative data centers are generally equipped with managed PDUs since their switching capabilities improve reliability. However, simply installing managed PDUs is not enough – an “unmanaged” managed PDU will actually reduce reliability.
So how do managed PDUs work? These advanced units offer a series of configurations which – if properly implemented – improve the availability of important services. The main features are Software Over Temperature Protection (SWOTP) and Software Over Current Protection (SWOCP), which are well described in the blog post “Considerations for a Highly Available Intelligent Rack PDU”.
It is also well-known, that managed PDUs can support commissioning or repairing workflows in data centers. The combination of well designed workflows and managed PDUs pushes the operational reliability to a higher level.
In high performance data centers, using clusters, another important point comes into play: clusters are complex hierarchical structures of server farms, which are able to run high performance virtual machines and fully automated workflows.
As described here or here, such clusters are managed by centralized software together with server hardware.
Over the last couple of years cluster solutions have been developed following strong and challenging availability goals, in order to avoid any situation, which make physical servers struggle within the cluster. However, there would still be the risk of applications and processes generating faults and errors and screwing-up the complete cluster, unless there was an automated control process – the good news is: there is.
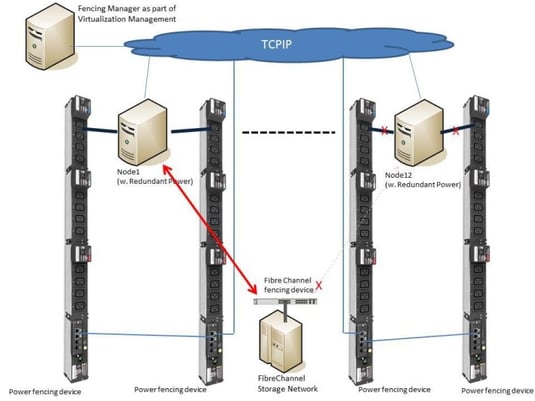
The process which controls those worst case scenarios is called fencing. Fencing automatically kicks out of the cluster any not working nodes or services in order to maintain the availability of the others.
Fencing has different levels, which are hopefully wisely managed. In a smooth scenario fencing will stop disturbing services, or re-organize storage access (Fibre channel switch fencing) to let the cluster proceed with its tasks.
Another power fencing option is also called “STONITH” (Shoot The Other Node In The Head) and allows the software to initiate an immediate shutdown (internal power fencing) of a node and/or a hard switch off (external power fencing).
The internal power fencing method uses IPMI and other service processer protocols, while the external power fencing uses any supported network protocol to switch of a PDU outlet. It is recommended to use secured protocols only, such as SNMPv3. So managed PDUs as MPH2 or MPX do not only support a nice power balance, monitor power consumptions or support datacenter operations workflows – they also allow the fence software to react quickly for higher cluster reliability. So it’s not a secret that cluster solutions manufacturers – e.g. Red Hat with RHEL 6.7 and newer – openly support such managed rack PDUs.
For More Emerson Network Power Blogs, Click Here
Topics: Data Center, PUE, robust data center, Containment, efficient data center, DVL, electrical distribution, energy, Battery, Thermal Management, energy efficiency, 7x24, PDU
by Emerson Network Power on 9/23/15 9:14 AM
Rick Holloway | September 23, 2015

The Federal Government’s 30-day Cybersecurity Sprint ended earlier this summer, but the real work continues. Government agencies and equipment manufacturers are awaiting the results of the ongoing cybersecurity review and the release of the Federal Civilian Cybersecurity Strategy – expected soon – but the preliminary principles of the strategy are intriguing on their own.
One thing that’s clear – and not at all surprising – is the government believes the approach to the increasing cybersecurity challenge is both behavioral and equipment-focused. There is no magic bullet piece of hardware or software that will provide adequate protection against all of today’s security threats, but a combination of threat awareness, adherence to best practices and deploying and properly using today’s hardened technologies can reduce risks.
There are eight key principles that will form the foundation of the Federal Civilian Cybersecurity Strategy. They are:
1. Protecting Data: Better protect data at rest and in transit.
2. Improving Situational Awareness: Improve indication and warning.
3. Increasing Cybersecurity Proficiency: Ensure a robust capacity to recruit and retain cybersecurity personnel.
4. Increase Awareness: Improve overall risk awareness by all users.
5. Standardizing and Automating Processes: Decrease time needed to manage configurations and patch vulnerabilities.
6. Controlling, Containing, and Recovering from Incidents: Contain malware proliferation, privilege escalation, and lateral movement. Quickly identify and resolve events and incidents.
7. Strengthening Systems Lifecycle Security: Increase inherent security of platforms by buying more secure systems and retiring legacy systems in a timely manner.
8. Reducing Attack Surfaces: Decrease complexity and number of things defenders need to protect.
I doubt anyone would disagree with those points. But what can we infer if we take a closer look?
It’s not called out specifically, but a consistent theme is access awareness and control. We live in a time when everything is connected—and needs to be, to ensure our data, our networks, our lives move at the speed the world demands. But every connection is an access point, and every access point is a potential vulnerability. Understanding where those access points are and securing them through both technology and best practices is a significant first step in securing a network. This can be as simple as proper credential and password controls.
The point about replacing less secure legacy systems with more secure, modern technologies is important. While there are limits to the effectiveness of software updates and patches, equipment replacement can be costly. Organizations that value security will put plans in place to upgrade equipment over time—and the sooner they start, the better.
One of the more interesting and encouraging points in the preliminary list is the bullet about recruiting and training cybersecurity personnel. This reflects a necessary awareness of the nature of these threats. They aren’t static; hackers are evolving and devising new attacks and tactics every day. It’s critical that our IT personnel maintain the same vigilance and dedication to security and threat education.
Of course, these are simply preliminary indications of the government’s thinking. We’ll know more when the Federal CIO releases the final Federal Civilian Cybersecurity Strategy, and we’ll take a closer look at that strategy and what it means at that time.
For More Blogs and News from Emerson Network Power Click Here
Topics: Data Center, Thermal Management, DCIM, monitoring, cybersecurity, security
by Marissa Donatone on 9/11/15 1:28 PM

Date: Wednesday, September 30, 2015
Time: 12:00 Noon - 12:50 PM EDT
More and more, data center professionals are struggling to reconcile the demand for faster operational deployment, while delivering the high availability standards required of their customers.
Data center leader, Expedient, has nurtured a set of best practices to consider. Director of Facility Engineering, Ed Dzurko will share his thoughts and insight on how they utilize electrical configurations, technologies, and services to deliver a more standardized solution to meeting design and operational goals.
Join Ed and Network Power’s Brian Kennedy as they explore electrical power system designs, configurations and practices for powering critical data centers.
Topics: Data Center, power, power system
by Emerson Network Power on 8/19/15 8:49 AM

From major retail cyberattacks to Hollywood studio hackers, cybersecurity is now, more than ever, on the mind of every CIO in the world — and rightfully so. According to our recent article in Data Center Journal, the most common cause of a data breach is malicious or criminal attacks, which could end up costing not only nights of sleep for CIOs, but also millions of dollars; in some cases upwards of $5.4 million.
While these attacks can be devastating, there are some best practices to help avoid cyber-disaster:
1. Don’t give hackers a back door: In order to prevent data breaches, consider isolating your network to avoid allowing easy access to your information. Since access can be logged through network isolation, unwanted activity can be monitored and flagged. To isolate your network and limit threats without compromising necessary access or performance, consider utilizing isolated out-of-band management networks. These networks provide full, real-time access without giving hackers back door entry.
2. Enforce the three A’s: Authentication, authorization and auditing are all critical to securing your network. Ensure your cybersecurity by using fine-grain user authentication through a centralized and controlled process, while still allowing easy access for administrators.
3. Ensure trust and best practices with outside vendors: Servicing data center equipment typically requires allowing atypical access to sensitive information about your data center with people outside your organization. Even new technologies are now requiring software updates while sharing IP addresses and network ports to accommodate those updates. While you may feel confident in your organization’s security practices, it’s also important you trust the security measures practiced by those outside parties or contractors, as well.
Security is a complex, never-ending process, but the right partners can help cut through that complexity and ensure your network—and your business—do not become the next victim.
What other best practices do you use to ensure your network is secure?
For more Blogs by Emerson Network Power, Click Here!
Topics: Data Center, PUE, UPS, DCIM, monitoring, Trellis, the green grid, cybersecurity
Philadelphia | Albuquerque | Boise | Denver | Harrisburg | Salt Lake City
Headquarters: 115 Sinclair Rd., Bristol, PA 19007
1-215-785-5950