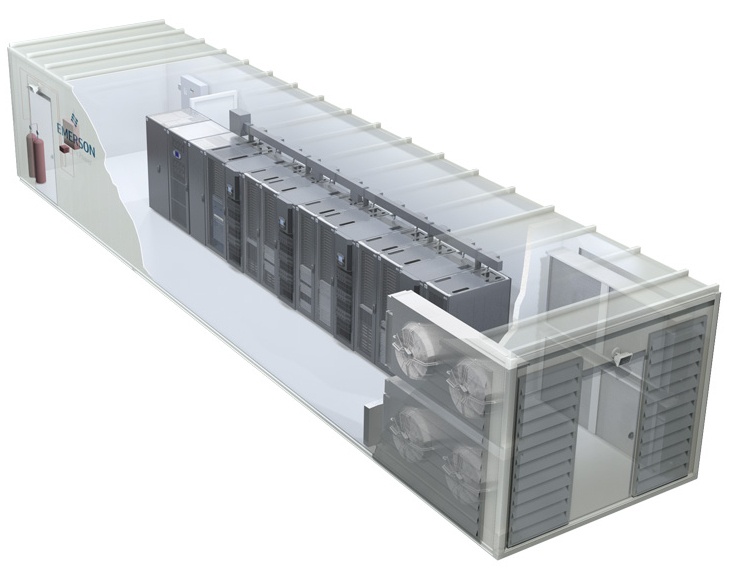
Some of our recent posts have highlighted the benefits of prefabricated data centers – here’s another one to add to the list: significant advancements in deployment, scalability and reduced life-cycle costs through the evolution of the edge of network. Where our networks were once divergent, assembly line-born systems of years past, we’re now starting to see a changing landscape with integrated, system-wide intelligence.
Prefabrication allows telco and IT providers to quickly deploy, add capacity, and locate computing closer to their end users without exceeding budget or compromising performance. For telco networks, prefabricated deployments at the edge of the network serve as aggregation centers for data that is regularly accessed. In other words, if files are stored in a prefabricated aggregation center somewhere closer to your home rather than the core site, it reduces latency and increases access speed. Or, more simply put, less buffering time or interruption while you binge watch the new season of Orange is the New Black on Netflix.
Corporations are also benefiting at the edge as prefabricated systems provide streamlined local computing for remote locations such as branch offices or small and medium businesses. By centralizing the applications these smaller offices frequently handle at their corporate data center, these compact, rapidly deployable systems will support local data storage and processing while providing secure remote monitoring and manageability. Thus, allowing small businesses to act more nimbly and give customers quicker responses and service.
At the end of the day, customized prefabricated facilities deploy 30 to 40 percent faster than traditional stick-builds, transforming the way IT and telco providers serve their networks at the edge. But while the benefits are abundant, prefabricated solutions may not be right for every facility. In a recent article, I shared three questions IT and telco providers should ask themselves when evaluating options for the edge of their network:
1. What is the value of rapid deployment?
2. How does site selection affect design?
3. What compromises must be made to achieve rapid deployment?
I still believe these questions stand true. Are there any others you think IT and telco providers should be asking when considering prefabricated solutions? If so, post them into the comments below.
Written By: Steve McKinney | July 29, 2015
For More Blogs by Emerson Network Power, Click Here







 Ralph Conklin, Product Manager, Aftermarket Solutions for Thermal Management Support, Emerson Network Power:
Ralph Conklin, Product Manager, Aftermarket Solutions for Thermal Management Support, Emerson Network Power: